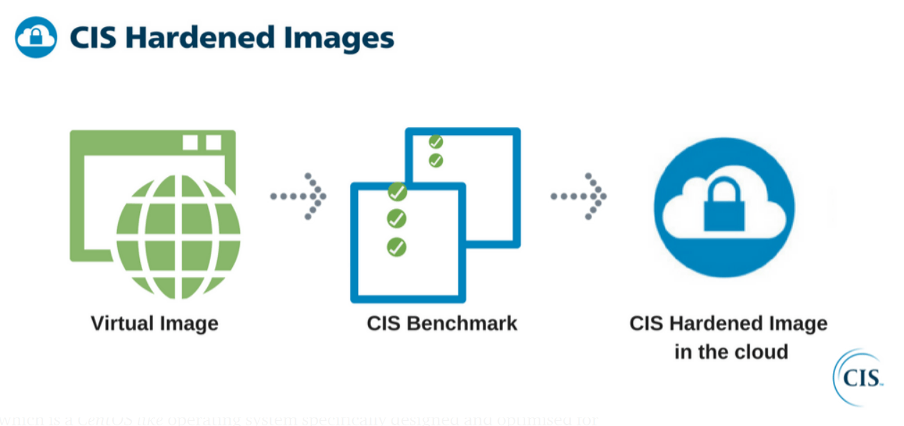
CIS Hardened Images for Cloud
CIS hardened images are a secure way to operate in a cloud and they are built off CIS benchmark security recommendation guidelines. In the cloud, if you need to have secure environments, you need to deploy the resources with such images for operating systems and your software that already have some security layer against some vulnerabilities. CIS hardened images, gives you the primary advantage of deploying the same high-standard image in mass deployments. It becomes easy to manage to update them all with regular security updates and patch management. Additionally, it ensures a secure environment across all the servers.
In many organizations I worked with, I have experience implementing the CIS Hardened Linux 2 AMIs from the AWS Marketplace for deploying. For example, say for a Pritunl VPN server EC2 instance. This shows that many organizations have started using the CIS Hardened images effectively on the cloud to ensure their application and data are safe. We should not forget that OS level security is more important than network level security because the cloud providers always ensure the use of advanced and updated network hardware and also it is easy to define network level security using the strong Firewall rules. But the application and data level security can be protected only when the OS level security is robust. CIS has its own built-in images for different cloud service providers. But those built-in images are a bit expensive. We can also build our own custom hardened images using the Python scripts provided by CIS that are also in compliance with CIS Benchmarks.
Container Image Hardening
Containers are everywhere nowadays and so are the images used to build them. A major challenge in containerization is the security of the image being used. Although in most cases you tend to develop custom images to be used inside the container, the possibility of a hacker injecting the malware into the images is also high. We need to be very careful in choosing the base image. There are several things to keep in mind before we build an image to use in the container.
The first step is to be conscious of using the network ports that you use to expose your application. Many troubleshooting sessions when the user is not accessible to the application involve changing the port and doing quick testing. In such scenarios, make sure you don’t forget to remove any extra ports you opened most importantly the one that is public internet-facing.
The second recommendation is to limit sensitive data such as secrets, passwords or any logs that share more details about the application configuration out of the build context. Better to use the docker ignore file to hide such sensitive information from the image build. In addition to that, it is recommended to keep the size of your base image as small as possible. This ensures that your application image would be less likely to be prone to any hacking attempts. Also, it is a good practice to run the containers in the read-only mode mainly in production and restrict the root user access.
Moreover, it is highly recommended to set up the architecture where the front-end web servers should be isolated from the backend systems. Because the database services should never be exposed to the public and the connections should also be granular. This will mitigate the risk of your application being exposed to security breaches. Eventually, it is always recommended to use a container orchestration tool preferably Kubernetes as it has its own security strengthening best practices and guidelines.
Conclusion
Hence in the world of microservices, the use of images is inevitable and they are used very extensively. The more we use images the higher the possibility of them being vulnerable. Therefore image hardening has become a mandated process in all the major compliance frameworks such as HIPAA, PCI-DSS and FedRamp and so on.
I hope this blog post is very useful to understand what Image hardening is, how CIS provides hardened images on the cloud and how to harden the container images at a high level. Please do follow me on below social forums for more such technical posts.

