Introduction:
F5 BIG-IP Application Security Manager (ASM) is a web application firewall that protects web apps and data from known and unknown security threats, vulnerabilities and bots. BIG-IP ASM is a powerful web application firewall that protects against complex threats as well as this also improves app performance by offloading SSL.
🎯𝐒𝐲𝐥𝐥𝐚𝐛𝐮𝐬
- 📌 Setting Up the BIG-IP System
- 📌 Traffic Processing with BIG-IP
- 📌 Web Application Concepts
- 📌 Exploiting Web Application Vulnerabilities
- 📌 Policy Tuning and Violations
- 📌 Attack Signatures and Threat Campaigns
- 📌 Positive Security Policy Building
- 📌 Security Cookies and Other Headers
- 📌 Automatic Policy Building
- 📌 Deploying Layered Policies
- 📌 Layer 7 DoS Protection
- 📌 Advanced Bot Defense
- 📌 Deploying BIG-IP Data Safe
BIG-IP ASM Specialist can easily deploy, tune, and operate BIG-IP ASM to protect their apps against HTTP based attacks. It gives out of the box protection for applications like Microsoft outlook, Microsoft office share point, Oracle e-business financials.
Did you know? The BIG-IP ASM was the first WAF to integrate with a scanner. WhiteHat approached all the WAFs and asked about the concept of building a security policy around known vulnerabilities in the apps. All the other WAFs said "no"...F5 said "of course!" and thus began the first WAF-scanner integration.
How does ASM work?
It provides the high level of security of applications. By means of the deep analysis of traffic of applications the product reflects complex DoS and DDoS of the attack. BIG-IP ASM provides compliance to the fundamental international standards of security (PCI DSS, HIPPA, etc.).
BIG-IP ASM will ensure safety of services of the company in details analyzing traffic of applications at higher level, i.e. it makes the analysis of requests of HTTP/S, SQL, JSON and so forth. Such approach helps to detect abnormal and harmful requests to the application and to prevent the attacks of XSS, hijacking, SQL injection and so forth. Requests from the malefactor to the application are done not pass, it reduces load of servers and ensures the safety of applications which is not requiring change of their code (for example, a web resource).
BIG-IP ASM will help to provide protection against DDoS of the attacks that will save operability of applications and performance of their work, will allow to avoid financial losses and reputation losses for the company. The protection DDoS mechanisms implemented in BIG-IP ASM help to reflect DDoS of the attack:
- HTTP flood,
- Slowris,
- SSL renegotiation,
- others.
The ASM also utilizes Geolocation and IP address intelligence to allow for more sophisticated and targeted defense measures. You can allow/block users from specific locations around the world, and you can block IP addresses that have built a bad reputation on other sites around the Internet. If they were doing bad things on some other site, why let them access yours?
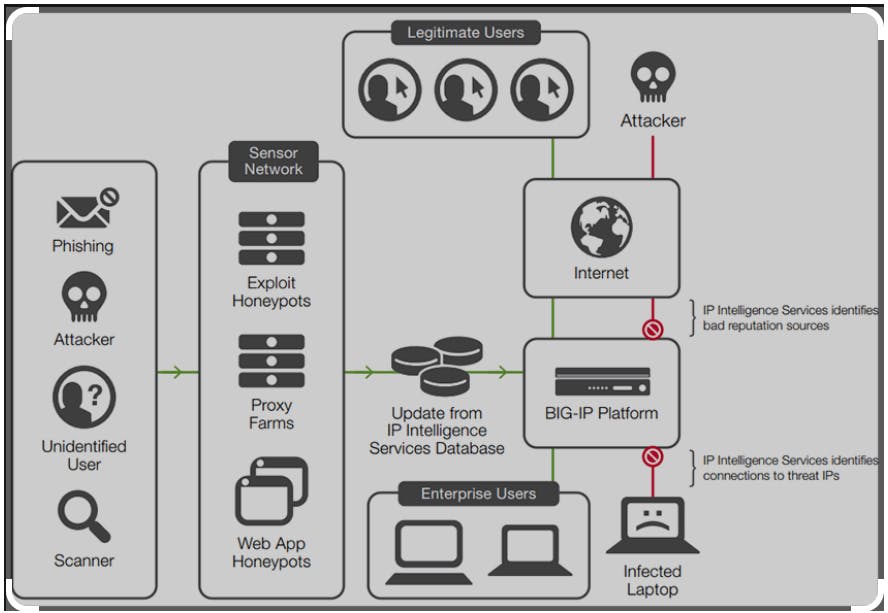
The ASM is also built for Payment Card Industry Data Security Standard (PCI DSS) compliance. In fact, you can generate a real-time PCI compliance report at the click of a button! The ASM also comes loaded with the Data Guard feature that automatically blocks sensitive data (Credit Card numbers, SSN, etc.) from being displayed in a browser.
The product is available as:
Hardware platform of BIG-IP
VIPRION chassis
Virtual device (BIG-IP Virtual Edition)
Summary :
(ASM) is a flexible web application firewall that secures web applications in traditional, virtual, and private cloud environments. BIG-IP ASM helps secure applications against unknown vulnerabilities, and enables compliance for key regulatory mandates.
If you have knowledge, let others light their candles in it. Happy Learning Always !
