Learn how IAM works
Identity Access Management performs Identity, Authenticate and Authorize as a key activities in the environment. Only the right person should have intended access to IT resources to perform an authorised tasks.
Why do you need IAM?
Security - If there is no IAM control implemented in a company, then the Information may be not secured, and anybody can access the information physically and logically which does not control the access.

Productivity – It increases the productivity of the IT resources as well as users as the IAM gives access to right people to right resources at right time, thus enabling to control the access and identity in a one stop as a Group /Role.

How Does IAM Work?
Identity access Management first identifies the users through their identity, authenticate using the Login credentials and then authorize their access to the IT resources/applications. This ensure that only intended users have access to the information. The IAM system denies if the user is not intended to access the information system.
Examples of IAM at your daily works:
- You are entering office and swiping your access card and it allows you to go through the Main door However, you cannot use the same card for going into a Server/Hub room because of access restrictions on your access card
- Similarly, a colleague of you who is supporting server team can use his/her card to get into Server/Hub room because he/she is supporting and has been granted access to enter.
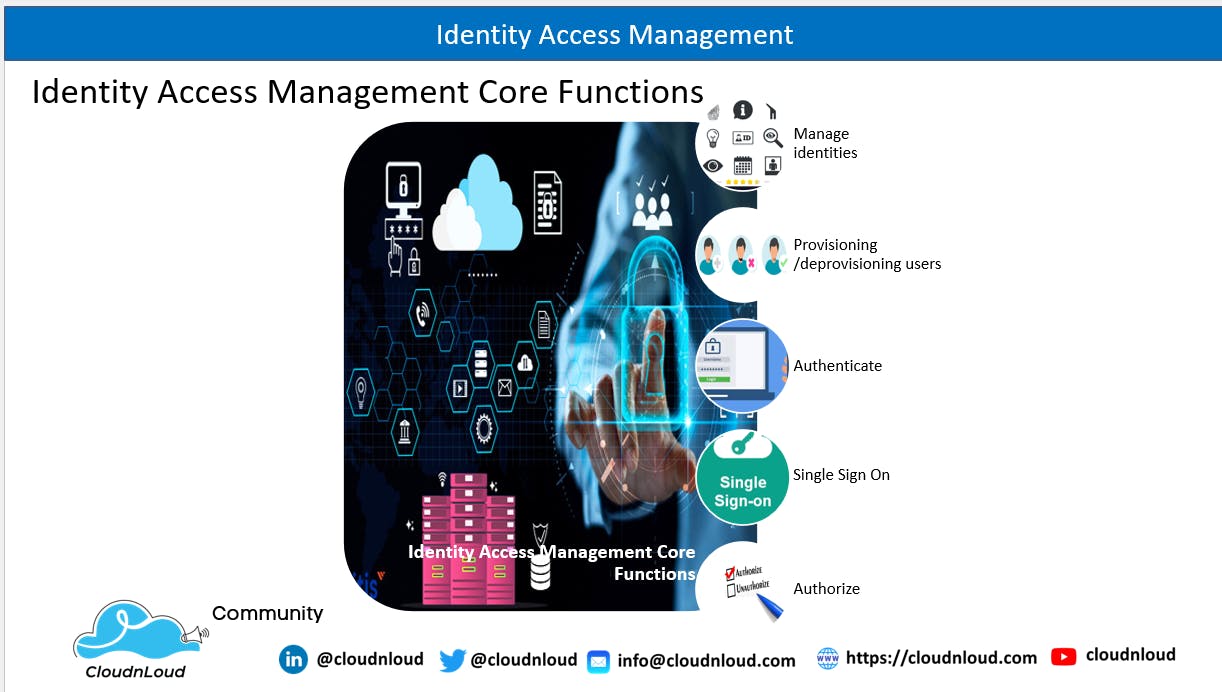
Core functions of Identity Access Management
- Manage user identities
- Provisioning and deprovisioning users
- Authenticating users
- Authorizing users
- Single Sign-On
What is the Difference Between Identity Management and Access Management?
Identity is confirming who are you and stores information about you. Example: your job role, designation etc., Access management uses information about your identity to determine your level of access to the systems and resources. Example: access to HR systems if your role/designation is manager but limited to level that you can manage the same for your direct reportees only.
