Recent breach on Uber proves costly and re ignited the need for zero trust approach in rapidly evolving technology space. Looks like Uber got used to these breaches, reputational damages, heavy penalties(Uber breaches Article link). But how these companies survive? If we see latest IBM report, the average cost of data breaches reached all-time high.The average cost for data breaches rose 2.6% from $4.24 million in 2021 to $4.35 million in 2022.Also a recent report from Norton security confirmed that Uber data breach affected 57 million riders and drivers PII data. Interesting fact is , now company started recruiting more security people :)
 I will quickly jump into the incident with below steps involved and also attack tactics the attacker used.
I will quickly jump into the incident with below steps involved and also attack tactics the attacker used.
Incident analysis: What really happened ??
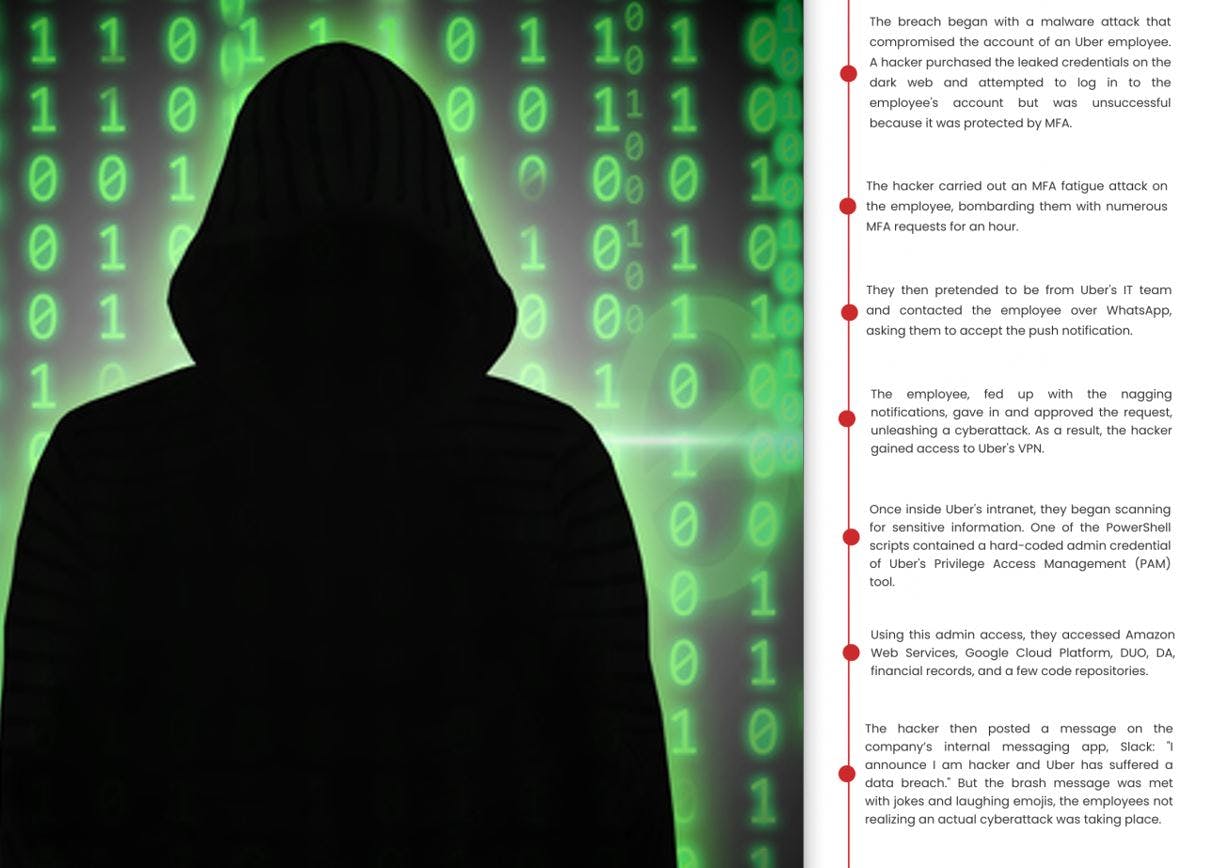
- It all started with an Uber external contractor #Compromise Accounts.
- It is likely, the attacker bought the contractor’s Uber Corp credentials on the dark web or forums #Reconnaissance/#Credentials
- The Corp password was exfiltrated from contractor’s personal device using #Malware.
- The attacker subsequently made multiple attempts to log into the contractor's Uber account and slowly started #Multi-Factor Authentication Request Generation/#MFA spamming/#MFA fatigue attack/Spearphishing via service.
- Each time, a 2FA-two-factor sign-in approval request was received by the contractor, initially blocking access. Eventually, hacker #Socialengineering technique -contacted the contractor as Uber IT tech, advised him to accept one.
- The attacker successfully logged in and added his device to MFA. And gained access to Corp VPN as #Initial Access with #Valid Account/#External Remote Services
- Attacker started #Lateralmovement inside Uber's intranet (.corp.uber.com ) for resource #Discovery and got access to a directory with *#Network Share Discovery.
- He scanned for hard coded passwords for #Credential in files in available scripts using #Credentialdumping patterns on the drive.
- He gathered the plain text admin credentials in a powershell script and started Privilege Escalation on #Domain Accounts and accessed their internal PAM solution-Thycotic.
- Moreover, the threat actor got access to all accounts and he shared(Exfiltration) several snaps/reports of Uber's internal environment including their AWS, GSuite, VCenter, Sale metrics, Slack, EDR and vuln portals reports.
- It was believed that Lapsus$ group involved in this activity.
Timeline view:
Lessons for every security teams:
Lack of Digital security hygiene costs a lot. Predicting and analyzing the organizational risk , recertification with valid IAM roles, continuous monitoring and testing of environment and lastly cybersecurity need executive buy in with regular assessments helps organizations with good digital hygiene. Below are the lessons from this attack.
- MFA is Not considered as Security Boundary any more, need a relook
- Avoid Using Static Credentials(IAM user Keys or service account keys)
- Avoid Sensitive information in plain text
- Effective Security implementation must Be Done in Layers (Defense in depth analysis)
- Social engineering is biggest threat, all employee & contractors needs training
- Now a days Security Tools have become a Double-edged Sword. Misconfiguration are the primary concerns.
More in-depth details and Security Usecases will be shared in coming blogs. Stay tuned...
Community and Social Footprints
YouTube Cloud DevOps Free Trainings
The CloudnLoud community is a non-profit open source tech community, volunteer-run event presented by members of the CloudnLoud Community.

