Table of contents
- Privilege Access Management
- Privilege Monitoring
- How to Perform Access Validation and Recertification
- Privileged Risks – Why Privilege Access Management is Needed
- Privilege risk from IoT, DevOps, and Cloud environments
- Benefits of Privilege Access Management
- Best Practices:
- Community and Social Footprints :
📌 Learn Privilege access Management
📌 Learn Privilege monitoring
📌 Learn how to perform Access validation and recertification
📌 Importance of Privilege Access Management

What is Privileged Account/Access– Any accounts which have privileges to perform activities such as changing configuration/settings, scheduling activities such as Patching on the system, application, network, or any computer resources is a Privileged account.
Example: Administrator, Database Administrator, Appadmin etc
Tip/Principle: Keep always Least Privilege Model for the user to ensure only limited access is provided to perform specific or intended tasks and to avoid Excessive privilege risk.
Refer my earlier series -Blog about Principle of Least Privileges (POLP)
Privilege Access Management
It consists of cybersecurity strategies, policies, for applying the controls over the privilege access/account & permissions for the users/process and the system in the environment.
The goal is to ensure principle of least privilege is enforced.
Privilege Credentials Management – Storing the credentials of Privileged accounts in a secured database. The privilege credentials/password generally provide elevated access & permissions across the accounts and environments.
Access Management- Only authorized users can access the credentials using multi factor authentications/keys.
Security Monitoring- The privileged accounts are being monitored for the malicious activities and alert will be generated for the same.
Reporting- reports can be generated based on the alert generated on the privilege usage.
Session management- Secure connectivity is provided for the privileged access through PAM via RDS/SSH/HTTPS etc,
Benefits of implementing the PAM Solution in your Environment is to minimize/Avoid malicious usage of Privilege access.
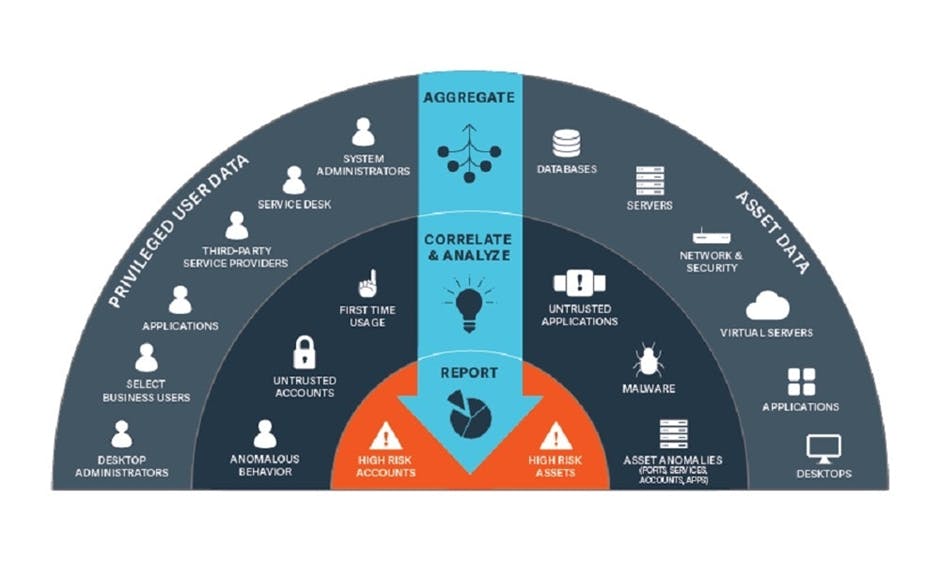
Privilege Monitoring
Certificates and Encryption: Used to verify and validate the users and applications. Used to encrypt the logon session in the environment initiated from client to server and vice versa.
Logging and Auditing: Logs needs to be in place for any privilege account activities. And should be readily available for audit as and when required.
How to Perform Access Validation and Recertification
- Access revalidation can be performed in various ways, using tools and automation.
- It is important that all the users/roles/groups in the environment undergo the revalidation to ensure the business need for the access/identity existing in the environment.
- It is also important for the privilege owners to revalidate/recertificate the access levels/ownerships given to the privileges within the environment
- Frequency of conducting the access validation and recertification should be stringent

Privileged Risks – Why Privilege Access Management is Needed

Existence of dormant/orphan IDs and privileges in the environment resulting in lack of visibility and awareness which pave way to backdoor attacks for attackers including old employee accessing the environment after leaving the company/org.
Excessive privilege resulting in risk of misuses and leaving attackers/hackers stealing the credentials to expose the environment and launching cyber-attack.
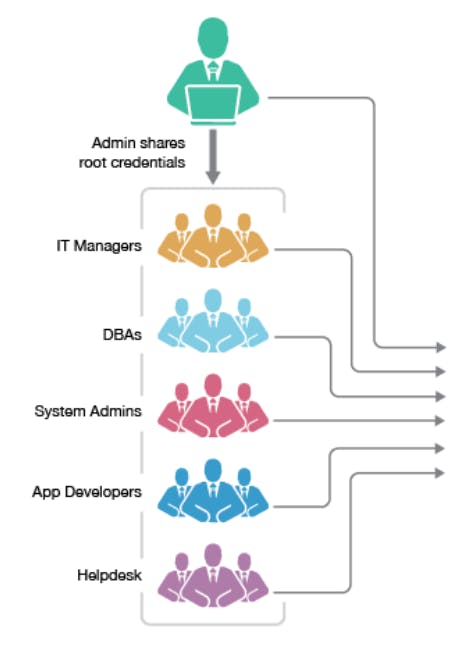
Shared account and password- where individual accountability cannot be tracked resulting in inappropriate usage of privileges and enabling seamless cyber-attacks.
With weak controls over the shared accounts/passwords it is impossible/difficult to track the logon /suspicious activities.
Siloed tools and processes -Due to multiple environment support there may be possible of losing the control over the IAM policies or processes and hence it is important to have a centralized control to privileges and accesses in the environment.
Privilege risk from IoT, DevOps, and Cloud environments

Cloud and virtualization administrator consoles & environments – Fast provisioning of user (s) access and privileges in emerging cloud computing increase the threat of Privilege access management. Organization need to ensure appropriate privilege security controls in place and implemented across the computing environment including network.
DevOps Environment- Emphasis on fast cloud deployment of software and application/automations where many challenges exists in privilege management. Often losing visibility and risks exposed in containers and other tools. Inadequate privilege management, password and excessive privilege leads to high risk in the application environment.
Edge Computing & IoT devices – Edge computing expanding to delivery faster data transfer enables a risk of securing the IoT environment and legitimate devices. IoT devices already have an existing security drawbacks such as default password, hardcoded and inability to harden the software/hardware/firmware. PAM is one of the best solution to avoid the risks around Edge computing and IoT devices.
Benefits of Privilege Access Management
A strong defensive control over the internal and external threats Reduced malware attacks Enhancing the Performance and operational efficiency. Easy to achieve and prove Compliant Help to avoid Cyber attack and satisfy cyber insurance requirements.
Best Practices:
- Establish precise privilege management policy
- Management of all privilege access and passwords with defined process
- Enforcement of Least Privilege across the accesses in the applications, network and computing environment.
- Enforcement of Separations Of Duties
- Ensure best password security practices
- Implementing Zero Trust Networks
- Monitor and audit all privilege activity
- Secure the automations of privilege workflows

