Table of contents
Today's episode deals with Data center components.
Server : Is a computer which serves or supplies the data or applications which are used by clients. Server names are based on 1) The functions they perform : E.g Application Servers, Web servers, Media servers. 2) The Platform (Operating system & Hardware) : E.g Linux servers, Windows Servers, Dell PowerEdge with Windows 3) The features : E.g Mainframe, Cluster, Virtual.
Firewalls : It is a network security system which based on predetermined rules controls and monitors the incoming and outgoing network traffic. This allows only legitimate traffic to enter the network. Types of Firewalls There are three types Software Firewall, Hardware Firewall and Both. Software Firewall : Also called as Host firewall is installed in the host device. Hardware Firewall : Also known as Appliance firewall. Is a separate piece of hardware which is placed between an internal and an external network
Based on the Method of Operation Firewalls are further named as : Packet-filtering firewalls : The most basic firewall type, the function of this firewall is to perform a simple check of all the data packets arriving from the network router and monitoring specifically IP addresses of Source and Destination, the Protocol, the Port number and any other surface-level data.
Proxy firewalls : Also called the Application-level Firewall filters the network traffic at application layer level to detect malicious traffic. This is an intermediary between two systems.
NAT firewalls : Network Address Translation popularly known as NAT firewalls. This assigns public address to a group of devices within a network, so the individual IP addresses are not visible to the attackers.
Web application firewalls : As the name suggests these are the ones responsible for monitoring, filtering and blocking the data packets which go to and for in a website or web App. The WAFs are available in the form of plugins, appliance or as cloud service.
Next-gen firewalls (NGFW) : This device combines the function of other firewalls.The next-gen firewall inspects the entire transaction of data, including the TCP handshakes, surface-level, and deep packet inspection.
IPS, IDS and VPN and how is it connected to Firewall.
A firewall filters traffic and so does IPS & IDS, so what is the difference?
The IDS (Intrusion detector system) is a monitoring system and hence will monitor the network for signs indicating cyber threats. The IPS (Intrusion Prevention system) is a control system and prevents traffic being delivered based on “signatures” The VPN (Virtual Private Network) helps the session to traverse public network through internet safely by encrypting the traffic.
 Storage : A process where in the computing technology helps store digital data within a storage device . This mechanism enables the retention of data temporarily or permanently.
Storage : A process where in the computing technology helps store digital data within a storage device . This mechanism enables the retention of data temporarily or permanently.
Storage Systems : such as hard-disk, solid-state, and robotic tape drives are important to helping any data center run these servers. Storage configurations
Direct-Attached Storage
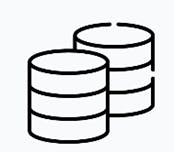
 In the Direct Attached Storage (DAS) storage configuration, devices like HDD and SDD are attached directly to the computers either internally or externally. DAS connects to a computer via an interface such as Serial-Attached SCSI (SAS), Serial Advanced Technology Attachment (SATA), Small Computer System Interface (SCSI), or Peripheral Component
In the Direct Attached Storage (DAS) storage configuration, devices like HDD and SDD are attached directly to the computers either internally or externally. DAS connects to a computer via an interface such as Serial-Attached SCSI (SAS), Serial Advanced Technology Attachment (SATA), Small Computer System Interface (SCSI), or Peripheral Component
Network-Attached Storage
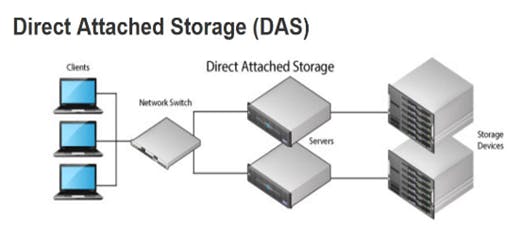
 In Network Attached Storage (NAS) configuration, the storage device is file-level which enables multiple users and applications to access data from a centralized system via the network. In NAS, users have a single access point that is scalable, relatively easy to set up
In Network Attached Storage (NAS) configuration, the storage device is file-level which enables multiple users and applications to access data from a centralized system via the network. In NAS, users have a single access point that is scalable, relatively easy to set up
Storage Area Network
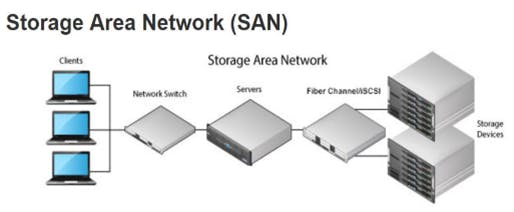
The Storage Area Network (SAN) configuration, a dedicated, high-speed network that interconnects one or more storage systems and presents them as a pool of block-level storage resources. Along with this SAN includes multiple application servers for managing data access and storage management.
Routers
Router connects devices to each other in hard-wired connection setups, to the modem. The router connects to a modem and then to devices (laptops, printers, etc.) via either an Ethernet cable or, WiFi signal. Routers, acts like the traffic police and is responsible for directing different types of networks to maintain the best transmission routes.
Routers can be either Wired or Wireless
Wired routers: Wired routers are older versions of routers with cable connections at both ends to receive and distribute data packets.
 e.g. LAN : A wired local area network established by a wired router.
e.g. LAN : A wired local area network established by a wired router.
Wireless Routers : Wireless routers, which transmit data directly to computers and other electronic devices via radio signals, are more advanced.
 e.g. WAN : A wireless local area network established by a wireless router.
e.g. WAN : A wireless local area network established by a wireless router.
Edge routers : These routers distribute packets across network and are located at the boundaries of the network
Core routers : These Distribute packets within the network and runs on the backbone of the internet and its jobs is to carry out heavy data transfers.
VPN routers : A VPN router is simply a router that has been configured to automatically connect to VPN servers, thus protecting your whole network.
Switches Switches forward data between devices Once a device is connected to a switch, the switch notes its media access control (MAC) address, a code that’s baked into the device’s network-interface card (NIC) that attaches to an ethernet cable that attaches to the switch. The switch uses the MAC address to identify which attached device outgoing packets are being sent from and where to deliver incoming packets.
Community and Social Footprints :
- Sunitha Shenoy
- GitHub
- YouTube Cloud DevOps Free Trainings
- Linkedin Page
- Linkedin Group
- Discord Channel
- Dev
Subscribe to our newsletter Read articles from Cloudnloud Tech Community directly inside your inbox. Subscribe to the newsletter, and don't miss out.

